Microsoft Azure AD®
You can integrate Microsoft Azure AD® (Active Directory) with Cloudflare Zero Trust and build rules based on user identity and group membership. Users will authenticate with their Azure AD credentials and connect to Zero Trust.
Set up Azure AD as an identity provider
Log in to the Azure dashboard.
Click Azure Active Directory in the Azure Services section.
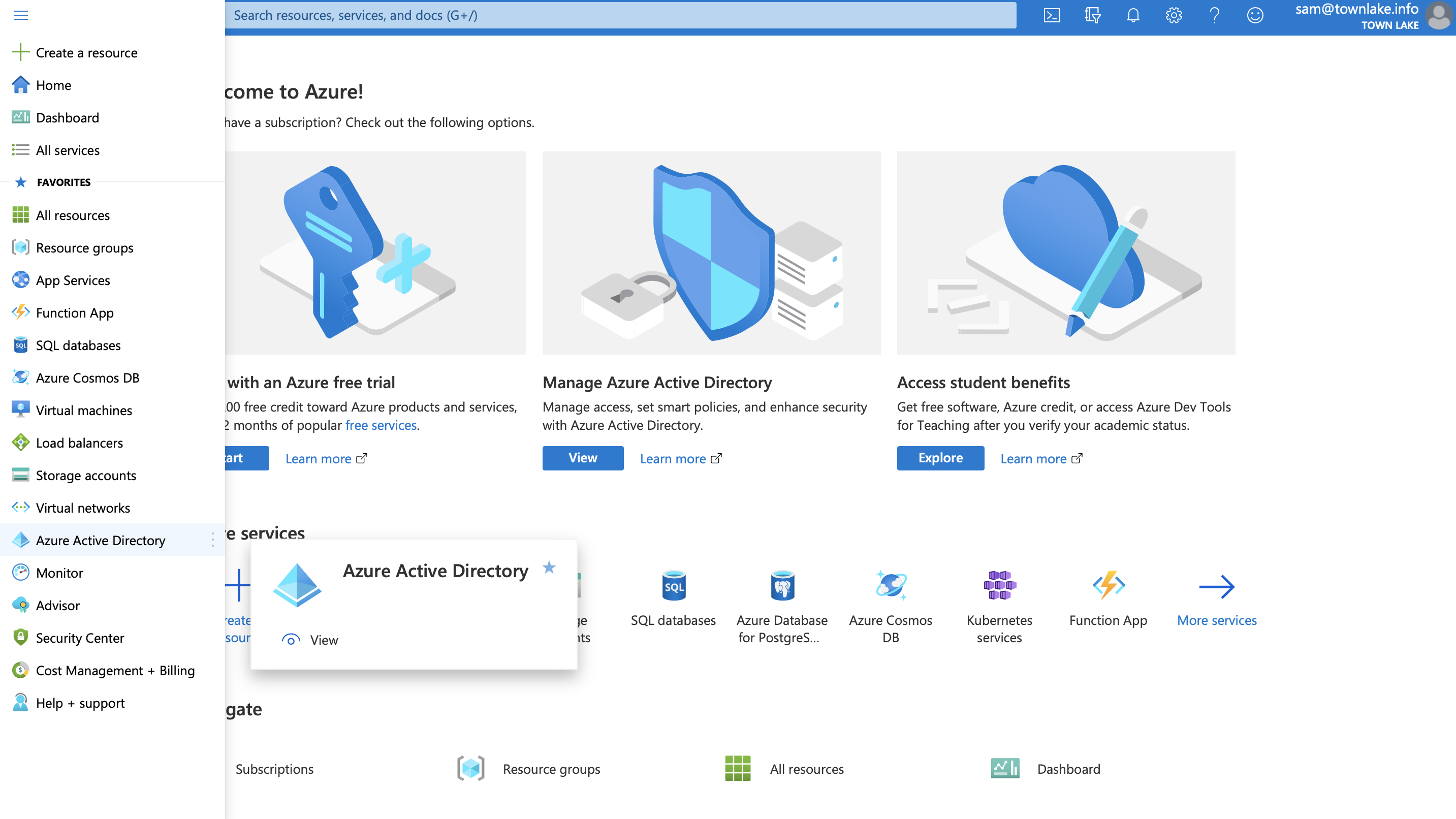
- Navigate to Manage > App registrations and click + New registration.
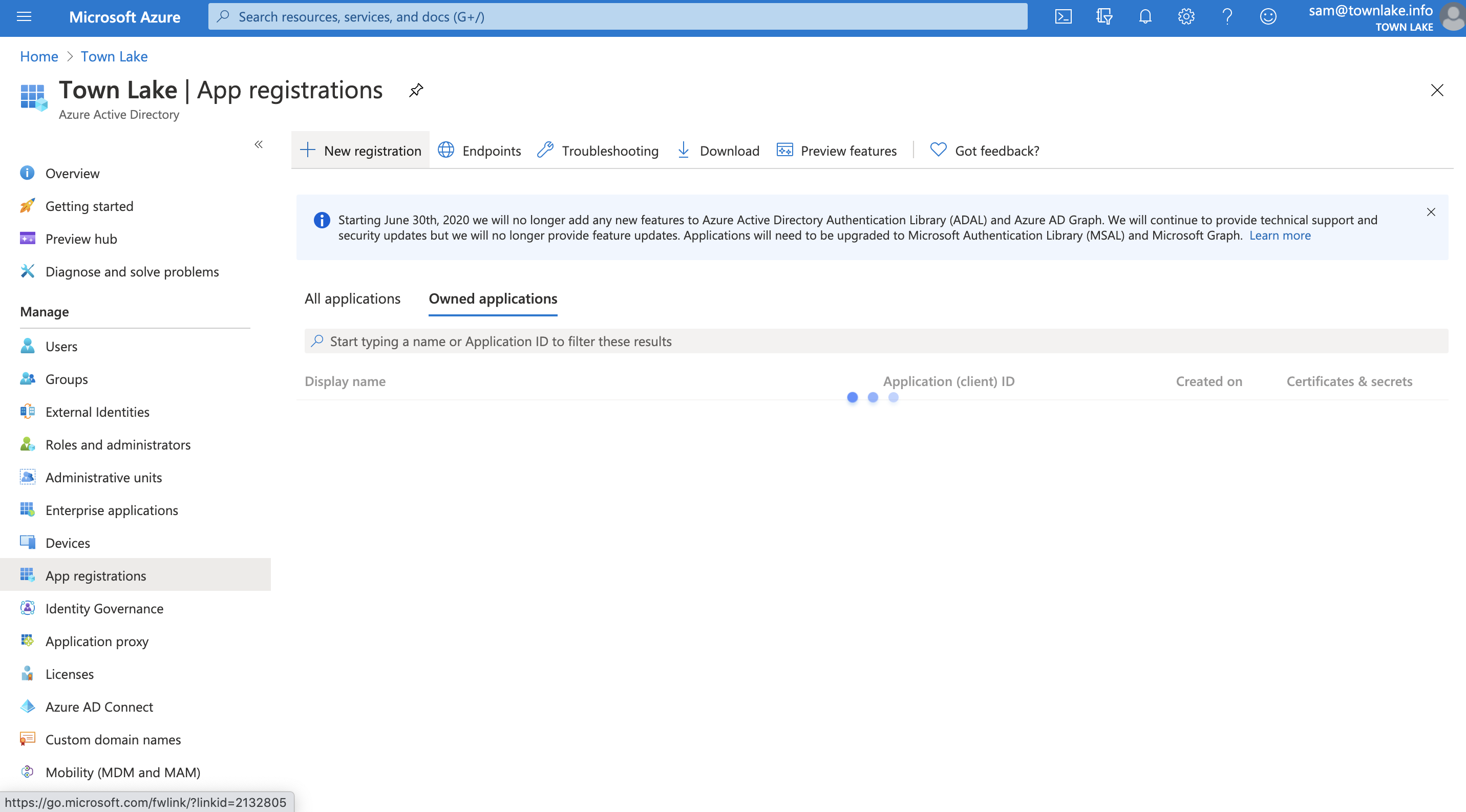
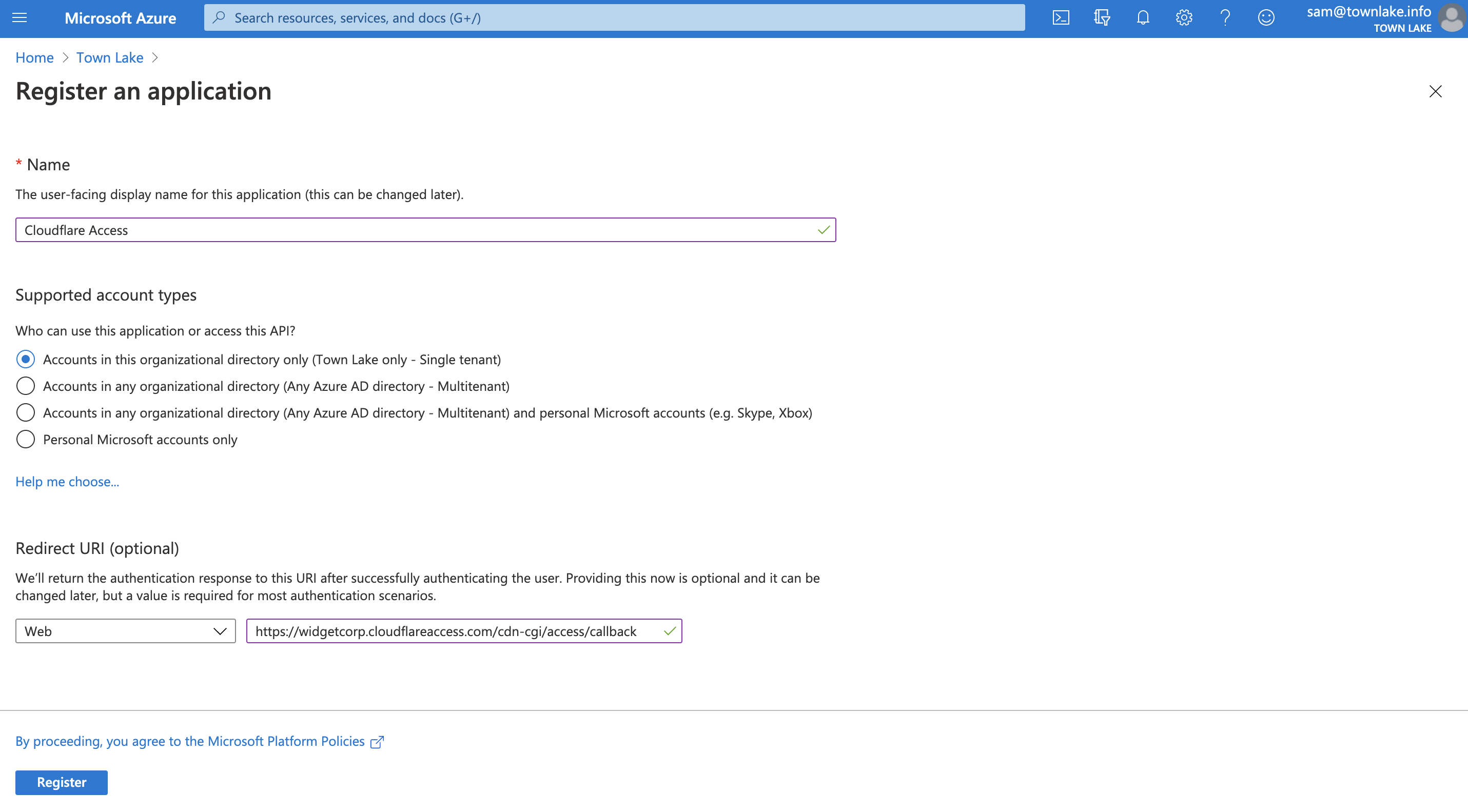
Name your application and select Web from the Select a platform dropdown.
Enter your team domain followed by this callback at the end of the path:
/cdn-cgi/access/callback. For example:https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/callbackClick Register.
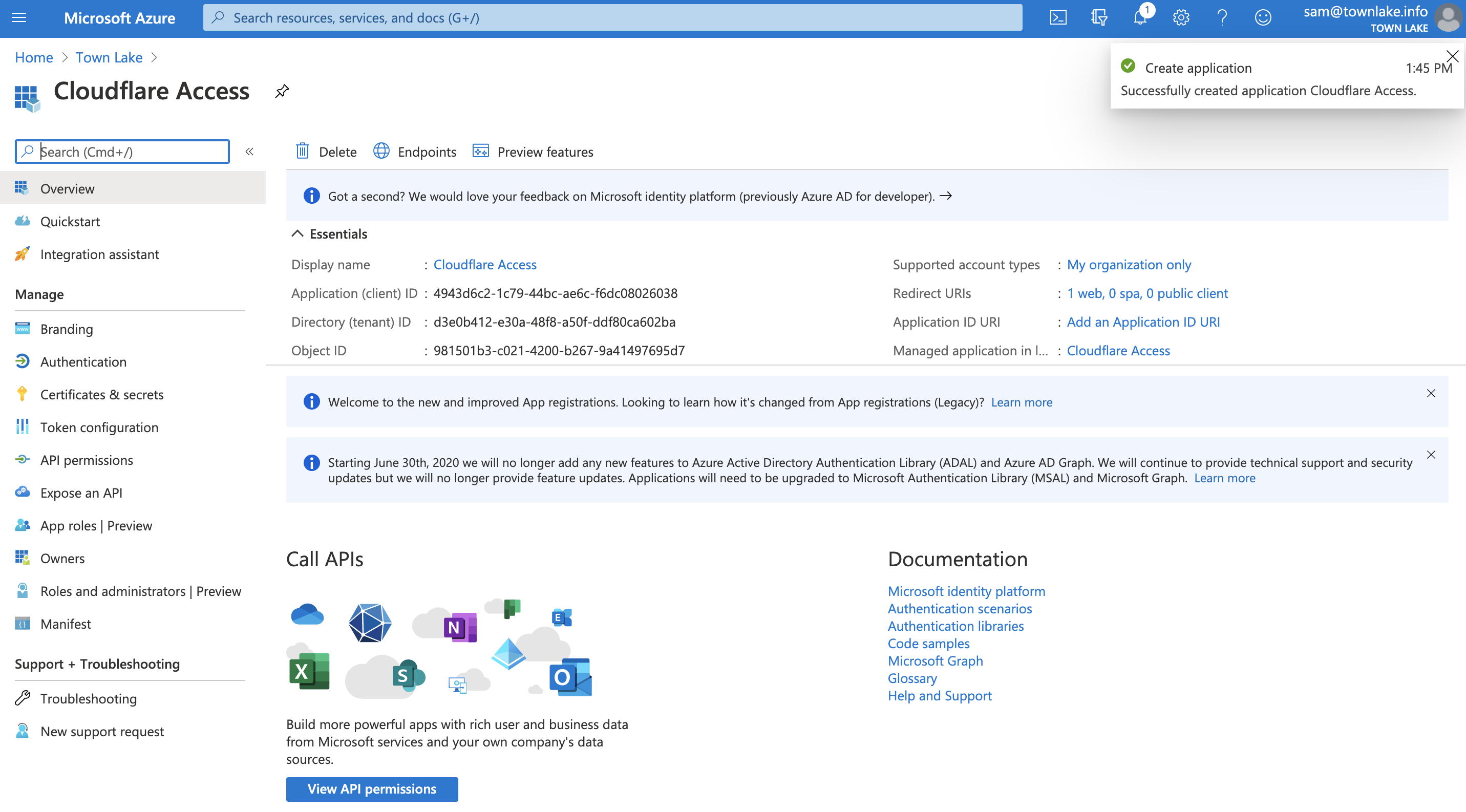
- Copy the
Application (client) IDandDirectory (tenant) ID. You will need to input these values into the Cloudflare dashboard.
To create an Application Secret, navigate to Certificates & Secrets and click + New client secret.
Name the client secret and choose an expiration. Click Add.
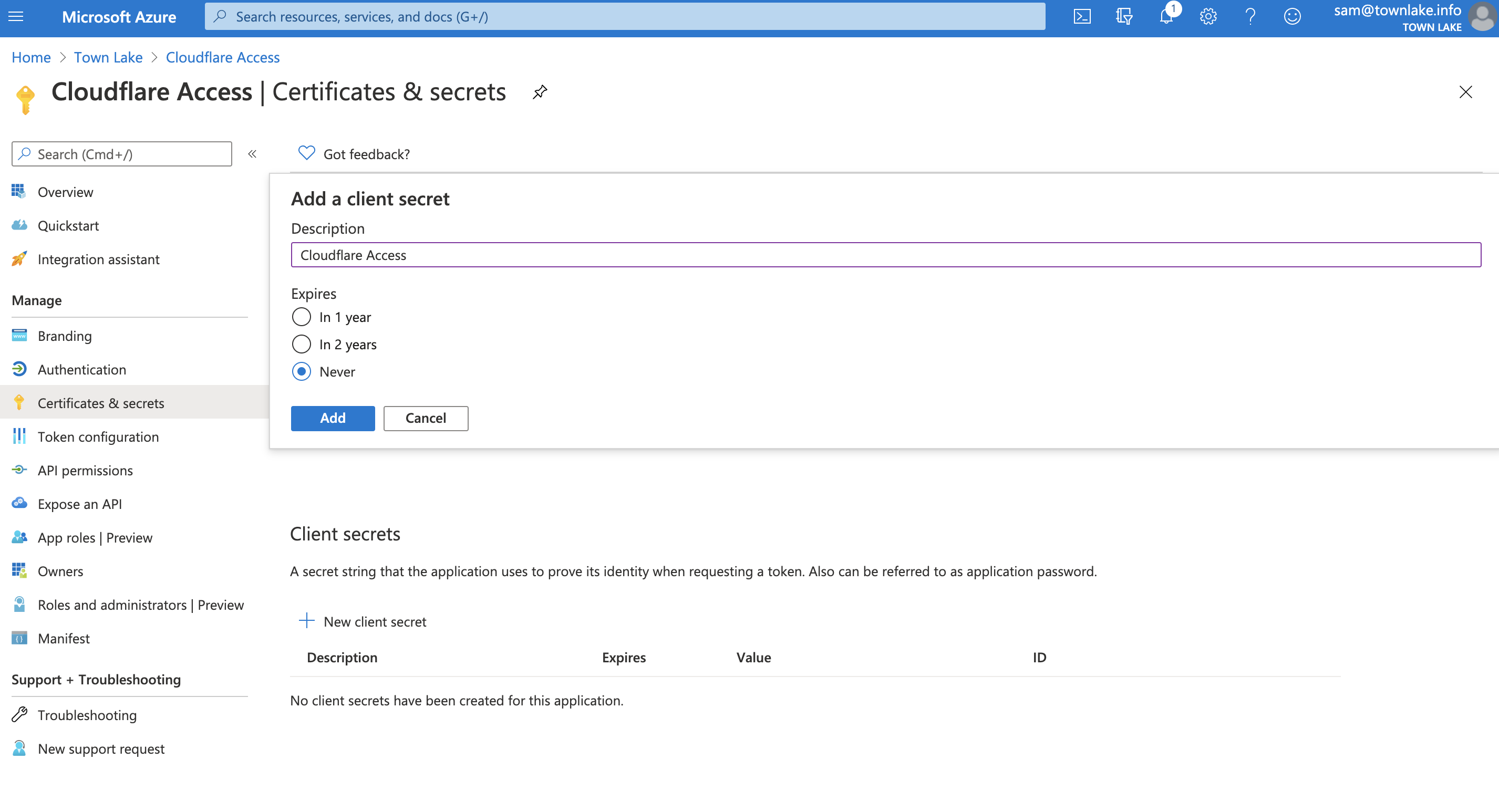
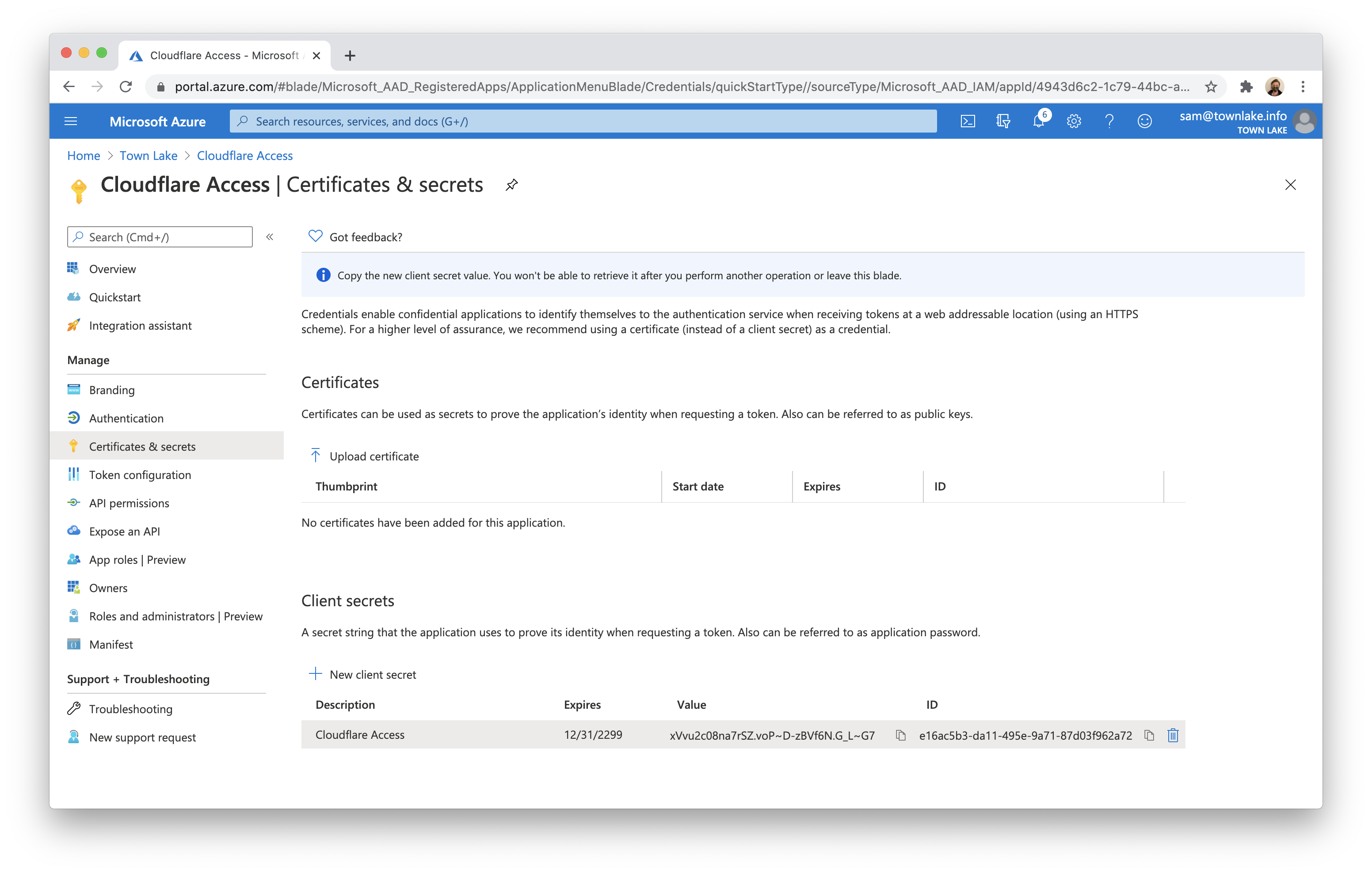
- Copy the
Valuefield of the client secret. Treat this value like a password. This example leaves the value visible so the values in Azure can be seen in the Access configuration.
- Navigate to API permissions and click Add a permission.
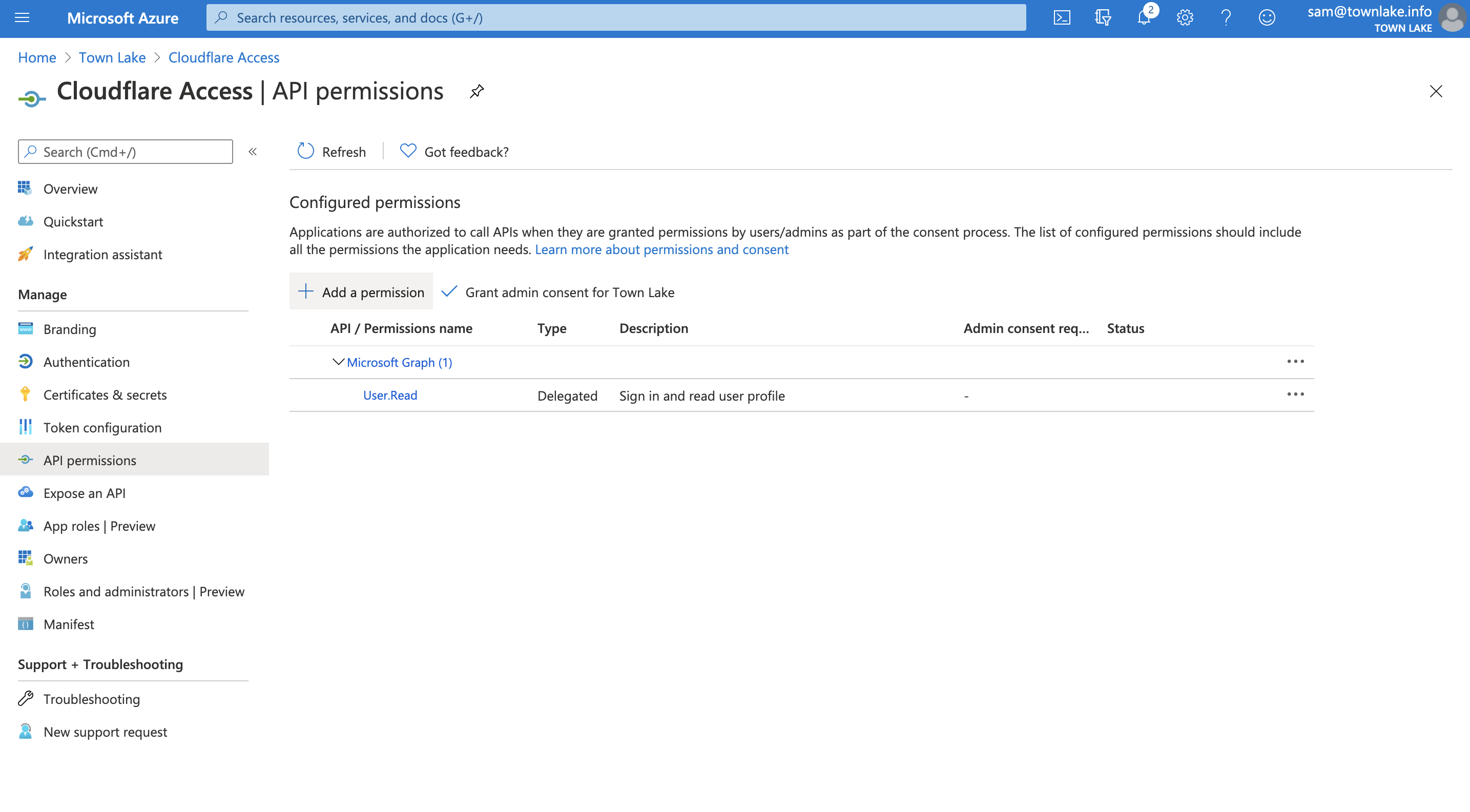
- Click Microsoft Graph.
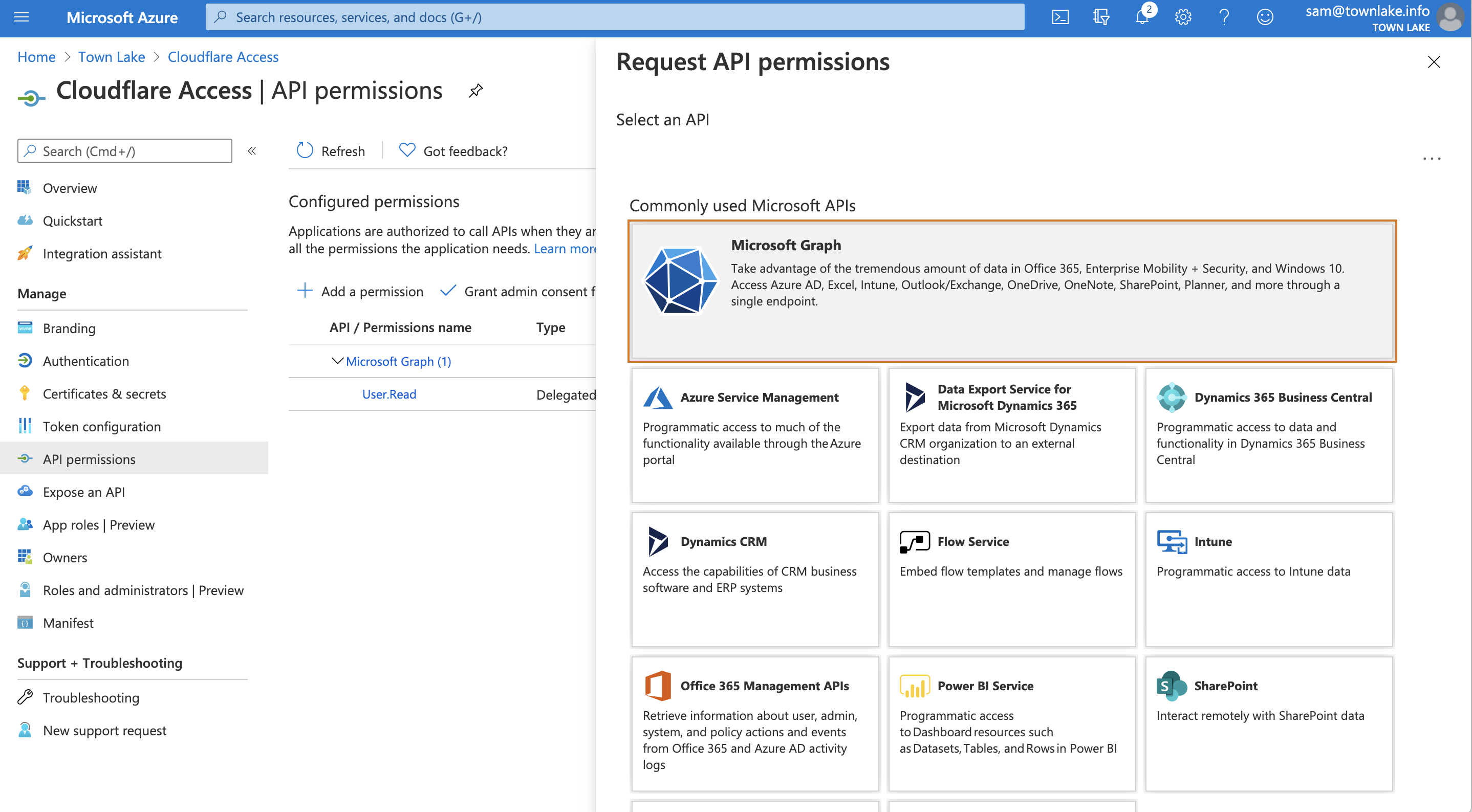
Select Delegated permissions. You will need to toggle 7 specific permissions in the next page. Once toggled, click Add permissions.
- openid
- profile
- offline_access
- User.Read
- Directory.Read.All
- Group.Read.All
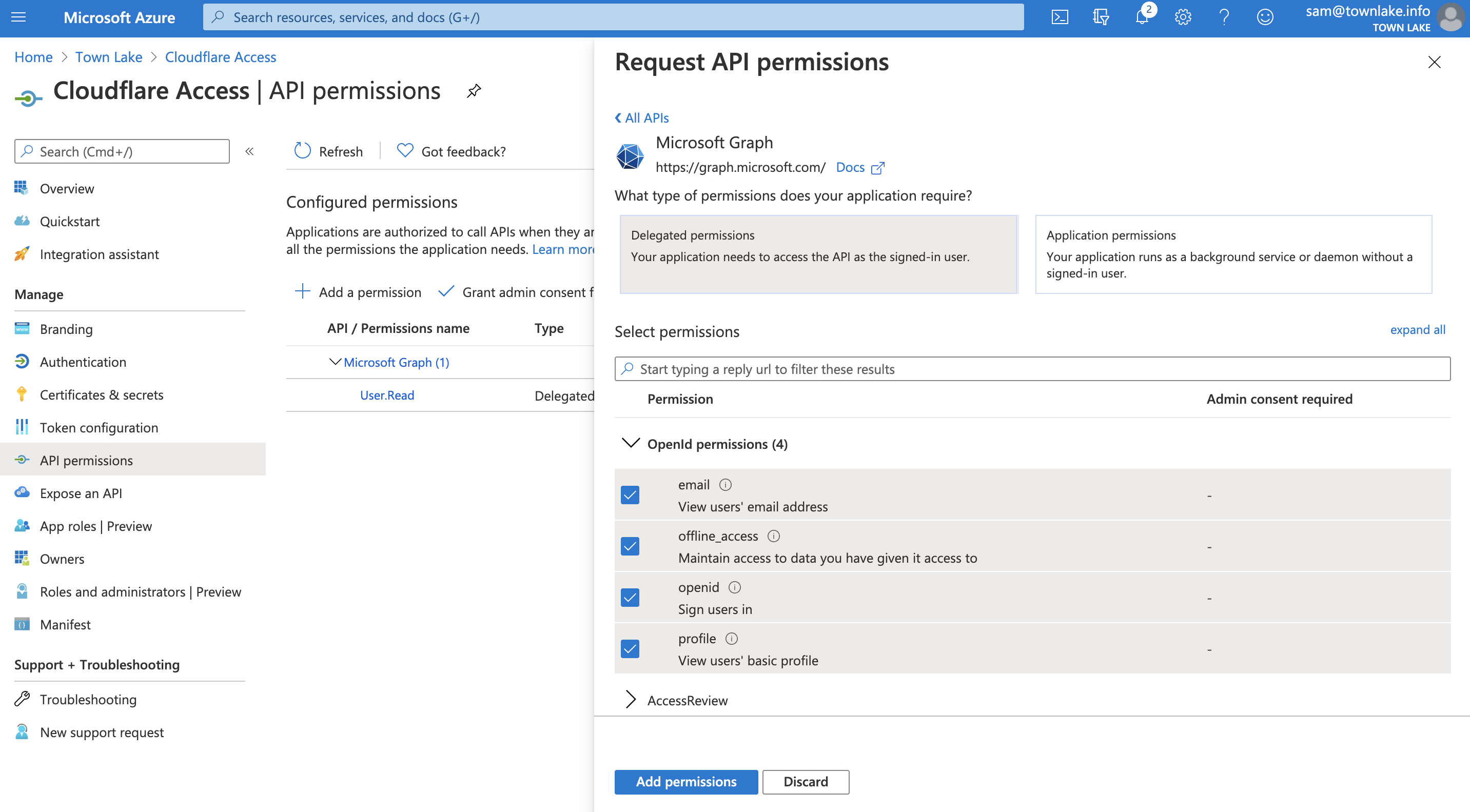
- Click Grant Admin Consent for
.
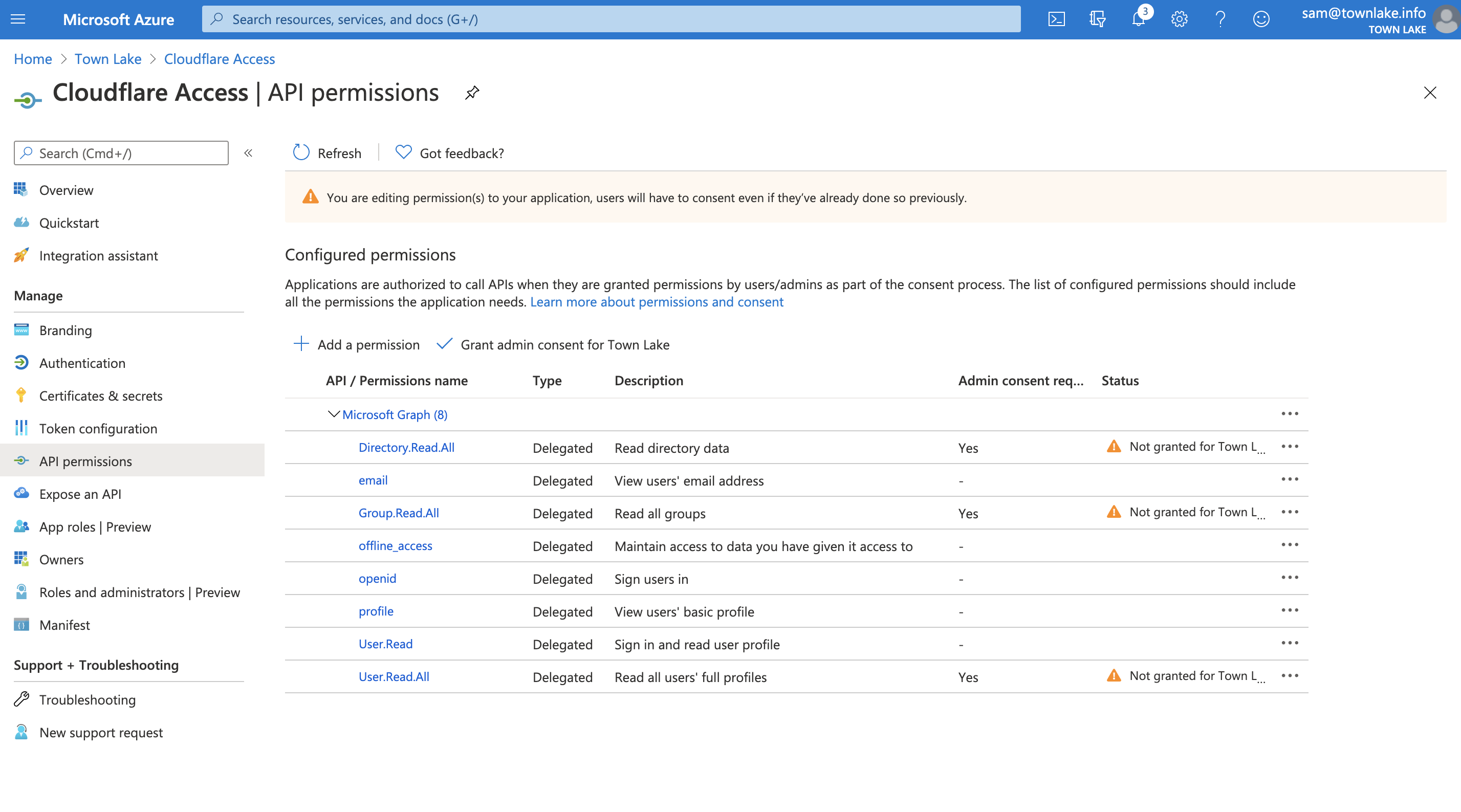
On the Zero Trust dashboard, navigate to Settings > Authentication.
Under Login methods, click Add new.
Click Azure AD.
Input the
Application ID,Application secret, andDirectory IDvalues from Azure.(Optional) If you are using Azure AD groups, toggle Support Groups slider On in the Edit your Azure AD identity provider window.
Click Save.
To test that your connection is working, navigate to Authentication > Login methods and click Test next to Azure AD.
Use Azure AD groups
Azure AD exposes directory groups in a format that consists of random strings, the Object Id, that is distinct from the Name. To use Azure groups in Cloudflare Access:
Make sure you toggle on the Support groups switch as you set up Azure AD on your Zero Trust dashboard.
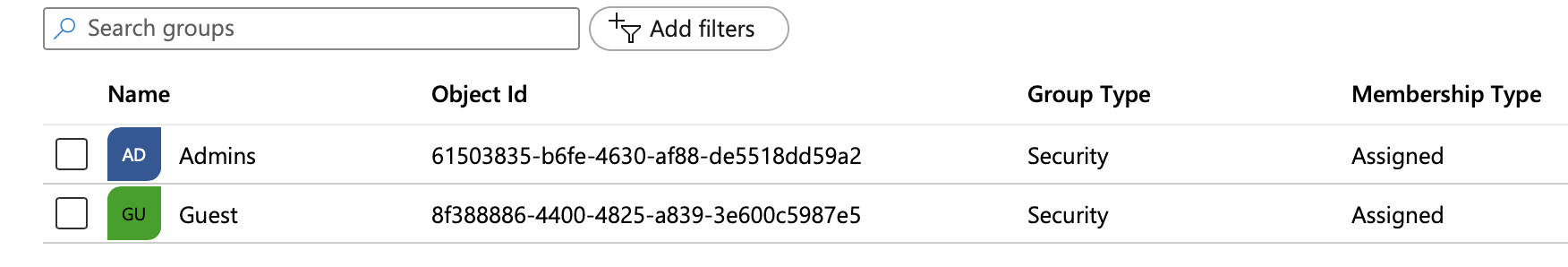
On your Azure dashboard, note the
Object Idfor the Azure group. In the example below, the group named Admins has an ID of61503835-b6fe-4630-af88-de551dd59a2.
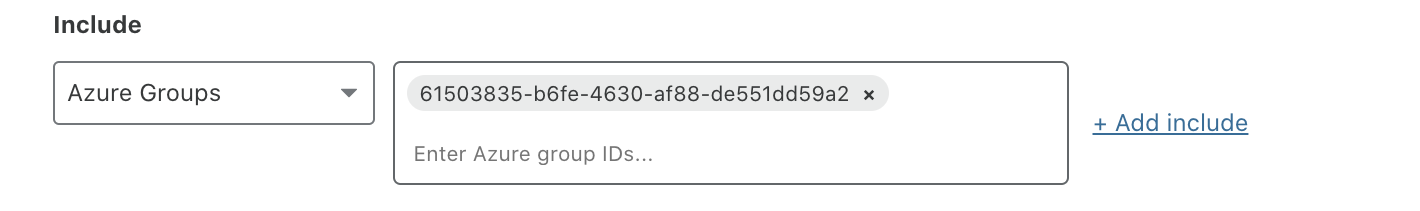
- When you create a Zero Trust policy for an Azure group, you will be prompted to enter the Azure group ID. Enter the
Object Idfor the Azure group.
Example API Configuration
{ "config": { "client_id": "<your client id>", "client_secret": "<your client secret>", "directory_id": "<your azure directory uuid>", "support_groups": true }, "type": "azureAD", "name": "my example idp"
}