You can integrate Google authentication with Cloudflare Access without a Google Workspace account. The integration will allow any user with a Google account to login (if the Access policy allows them to reach the resource). Unlike the instructions for Google Workspace , the steps below will not allow you to pull group membership information from a Google Workspace account.
Please note that you don’t need to be a Google Cloud Platform user to integrate Google Suite as an identity provider with Cloudflare Zero Trust. You will only need to open the Google Cloud Platform to access settings for your OIDC identity provider.
- Visit the Google Cloud Platform console. Create a new project.
Name the project and click Create.
On the project home page that loads, select APIs & Services from the sidebar and click Dashboard.
Go to Credentials and click Configure Consent Screen at the top of the page.
Choose
Externalas the User Type. Since this application is not being created in a Google Workspace account, the only types of users are external.Name the application and add a support email (GCP will require you to add an email in your account).
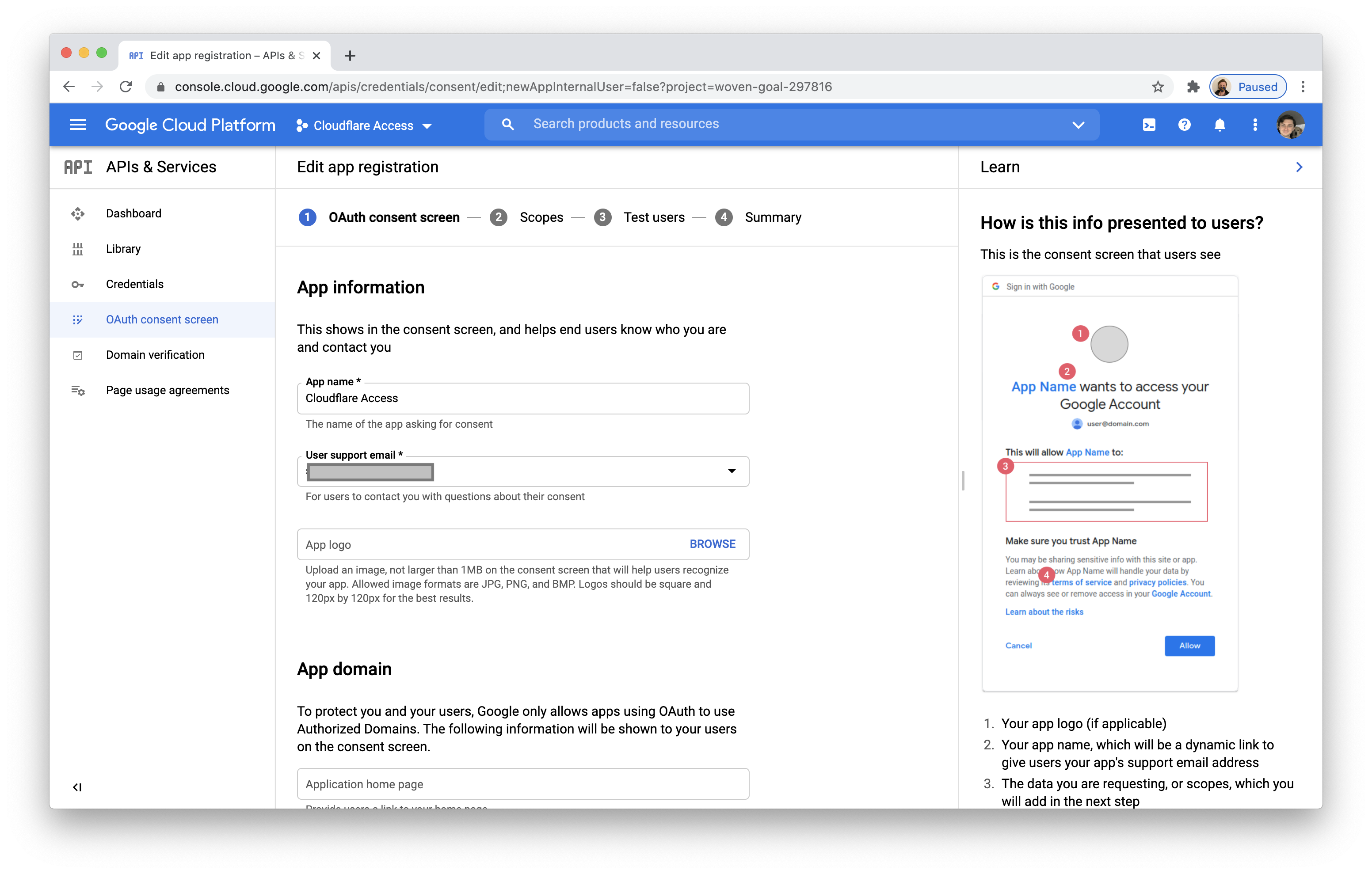
You will also be prompted to input contact fields.
- In the Scopes section, we recommend adding the
userinfo.emailscope. This is not required for the integration to work, but will indicate to users authenticating what information is being gathered.
You do not need to add test users.
You can review the summary information and return to the dashboard at the bottom of the page.
- Return to the APIs & Services page and click + Create Credentials. Select
OAuth client ID.
Name the application.
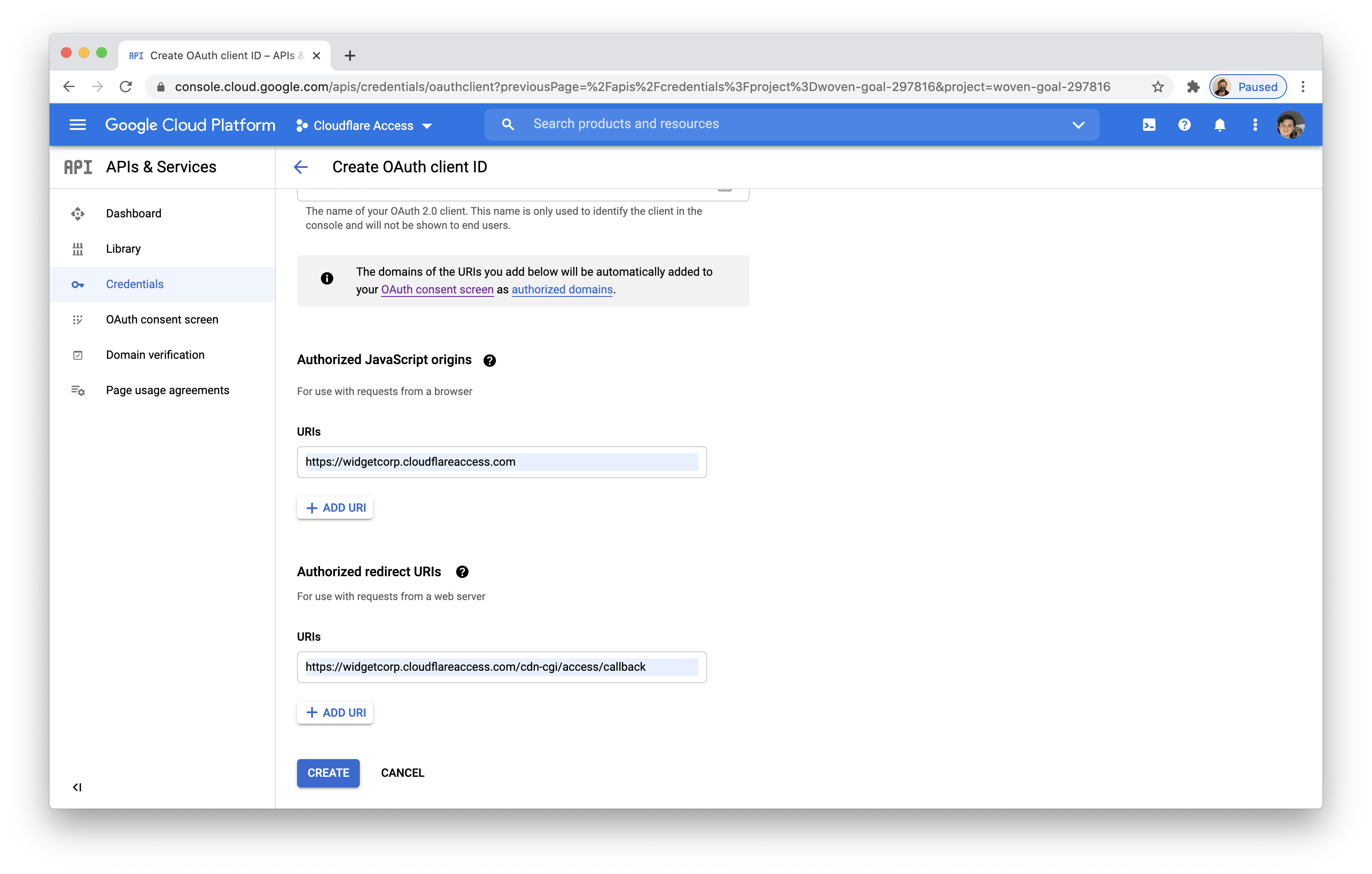
Under Authorized JavaScript origins, in the URIs field, enter your team domain .
Under Authorized redirect URIs, in the URIs field, enter your team domain followed by this callback at the end of the path:
/cdn-cgi/access/callback. For example:https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/callback
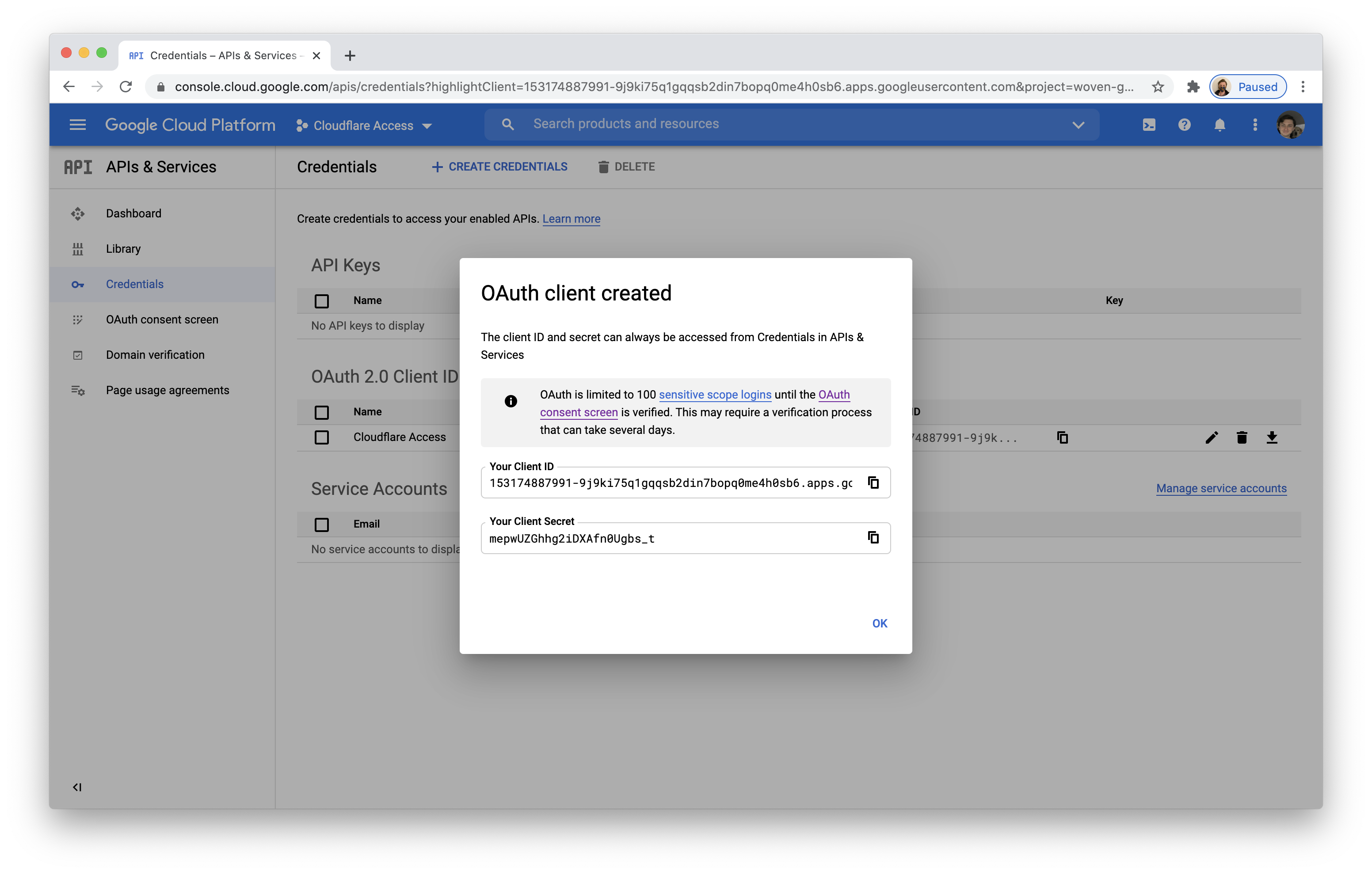
- Google will present the OAuth Client ID and Secret values. The secret field functions like a password and should not be shared. For the purposes of this tutorial, the secret field is kept visible. Copy both values.
On the Zero Trust dashboard, navigate to Settings > Authentication.
Under Login methods, click Add new.
Choose Google on the next page.
Input the Client ID and Client Secret fields generated previously.
Click Save.
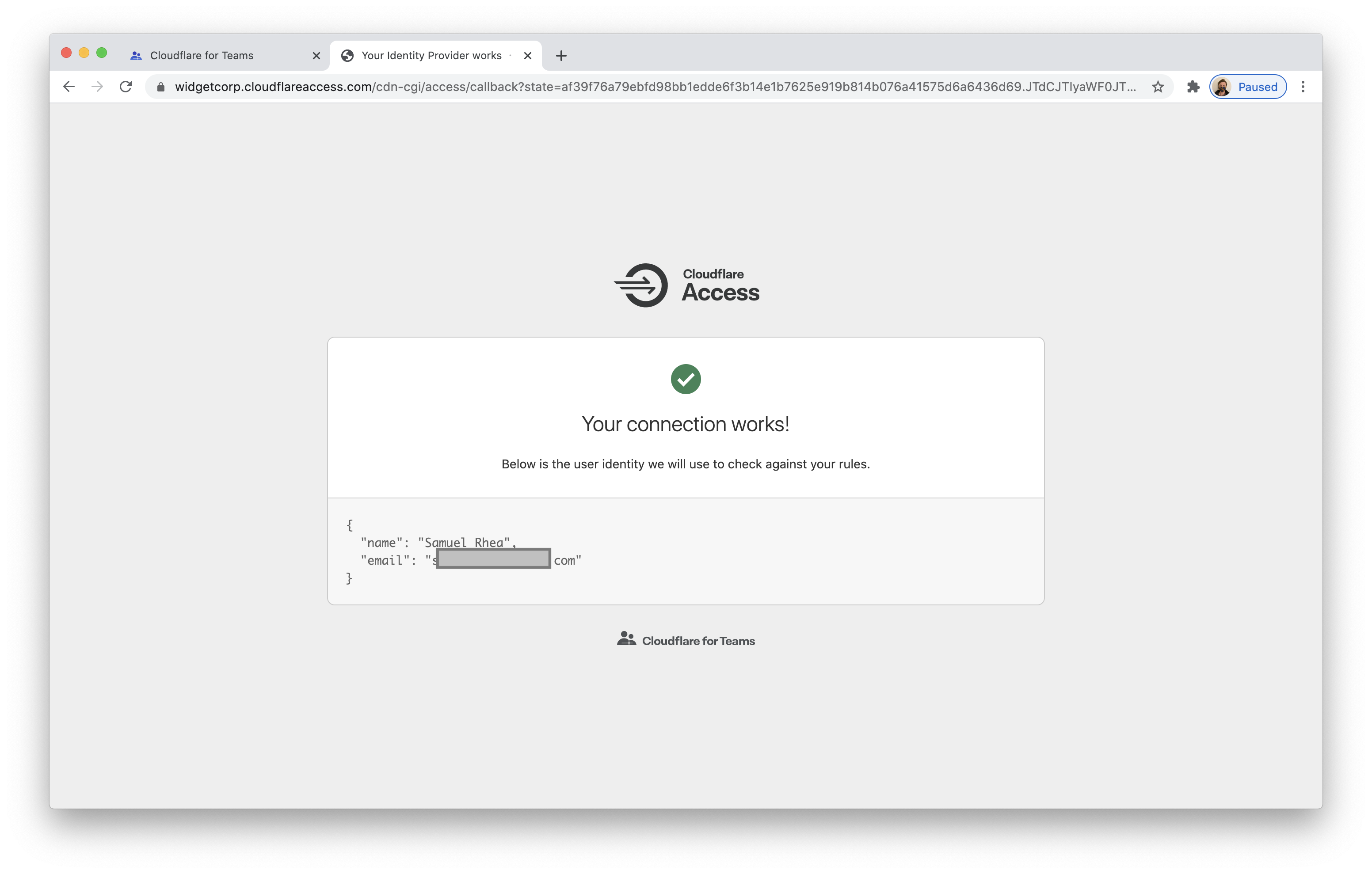
To test that your connection is working, navigate to Authentication > Login methods and click Test next to Google.
Your user identity should return.
Example API Config
{ "config": { "client_id": "<your client id>", "client_secret": "<your client secret>" }, "type": "google", "name": "my example idp"
}